Glossary of Abbreviations and Acronyms used in the security business
When I started working for IBM many years ago, all the new employees had to go to training classes. They taught us all about their products. I found that I not only had to learn about their technology but also about the abbreviations and acronyms they used.
When I left IBM to work at another engineering company, I learned that many of the abbreviations I learned at IBM were not used in the general industry. I had to learn a new set of abbreviations and acronyms. You may have also noted that the government has their own language.
Here are examples of some technical abbreviations and acronyms:
The language continues to change every day. Some abbreviations such as WWW are universally recognized, but others are unique to a technical area or organization. For example, MAC can stand for “mandatory access control,” “media access control,’ or “message authentication code.”
AC: Alternating Current, which is usually used to describe our standard 60 Hz 120 V power. Alternating current is an electric current that periodically reverses direction. We can thank Tesla for winning the war with Thomas Edison on power distribution. Edison believed that direct current (DC) was better while Nikola Tesla thought that AC was better.
ACL Access Control List is used with computer file systems. It provides the list of permissions attached to an object. Or, in the medical world, it’s the Anterior Cruciate Ligament. That’s the medical condition you don’t want.
AD Active Directory was developed by Microsoft to help manage all the users. It provides authentication and authorizes all users in a Windows domain type network. Of course, we have also seen this abbreviation used to define the epoch year for the Julian calendar.

AI Artificial Intelligence is machine-based intelligence that is attributed to computer devices. This contrasts with natural intelligence that is sometimes attributed to certain humans (and other animals).
ANSI American National Standards Institute is a private non-profit organization that manages standards for products and services in the United States. These are voluntary standards created at meetings where all the manufacturers tell each other that they don’t know anything, and then all yell at the government representative. Later they have coffee and donuts.
API Application Programming Interface is a set of instructions that can be used to interface with another program. It makes it easy for a programmer to add an application program that enhances the capability of the original program.
ASCII American Standard Code for Information Interchange is the binary coding used to describe characters, some graphic symbols, and control characters in a computer system. It all started with only five bits and has grown to seven bits. But since computers like to use bytes which are eight bits, the characters are defined with eight bits or one byte. Which is also equal to two nibbles (and maybe a bagel and cream cheese).
BCD Binary-coded decimal is a coding scheme that only defines the decimal numbers. We only need four bits to define all the decimal numbers. For those who need clarification, decimal uses ten digits because we have ten fingers. If you are an octopus, you can use octal coding.
BIOS Basic Input/Output System is firmware used in a computer system to perform the lowest level initialization of a computer. It runs some hardware checks and gets the computer ready for operation. The BIOS runs as soon as power is turned on and starts the main operating system. It gets Windows 10 or Mac OS booted and running.

Bit Binary digit is the information that computers use. It only has two values or states, a “1” or a ”0”.
I thought that Charles Babbage was the first to define this, but I just learned that Basile Bouchon and Jean-Baptiste Falcon invented the punch card (back in 1732). For those of you who don’t remember punch cards, they are stiff paper (cards) that had holes punched to represent a “one” while no hole was a “zero”.
In the early days of computing, a stack of these cards held your program. The first thing you learned was to number the cards so that you could put the stack together after you dropped them on the floor.
BNC The Bayonet Neill-Concelman Is a type of connector that is used with coaxial cables. There is a male and female end that connects with a quarter turn. The connector uses two bayonet lugs on the female connector. Many of the original analog surveillance cameras used this type of connector.
bps Is a measure of data transfer performance used in telecommunications and computing. It equals the number of bits over a unit of time. For example, the bit rate is quantified using bits per second. If we have a fast network, we like to see up to 1 Gbit/s (or 1,000Mbits/sec) data rate. We must be careful not to confuse this with B/sec which is Byte/sec. We use the “b” to define bits, and the “B” to define a byte.
Booting The boot program is a low-level program that gets the computer going. It’s like the starter in your car. This is like running the BIOS at initial power-on of the computer. Boot is short for Bootstrap. This is when the computer picks itself up by its own bootstraps and gets the operating system running so we can use it.
BW The bandwidth is the maximum data transfer rate across some connection. We usually define network bandwidth or digital bandwidth across a wired or wireless connection. We also measure the bandwidth consumption required by an IP camera. This abbreviation is also used by cameras that provide a black and white (gray-scale) image instead of a color image.

BW The bandwidth is the maximum data transfer rate across some connection. We usually define network bandwidth or digital bandwidth across a wired or wireless connection. We also measure the bandwidth consumption required by an IP camera. This abbreviation is also used by cameras that provide a black and white (gray-scale) image instead of a color image.
BYOD Is the policy of organizations that allow employees to bring their own laptops, smartphones, or tablets to work. It also means that my company is too cheap to buy me a new computer and want me to carry my own laptop to work.
Byte This is a unit of binary information that consists of eight bits. The byte was originally defined by IBM. Eight bits was convenient because it matched the early architecture of computers and provided enough information to encode a single character of text in a computer.
CAD Computer-Aided Design is used to help people design new things. It was first used to increase the productivity of drafting. The latest software systems go well beyond drawing and provide design tools that provide analysis and optimization of designs. The output of the system can be used to create manufacturing processes.
CAPTCHA Completely Automated Public Turing test to tell Computers and Humans Apart is a type of challenge provided by a computer program to determine if there is a human using the computer. Now I must prove I’m not a robot or if I’m a robot I have to prove that I’m a human. I’m so confused.

CCTV Closed Circuit Television is the original name for video surveillance. The concept provided video display on a limited number (closed) of monitors. This contrasted with video broadcast systems that were designed to be viewed by a large number of TV systems. The CCTV security system consisted of analog cameras, video mixers, and videotape recorders or DVRs. They were all connected using a coax cable.
CMOS Complementary metal–oxide–semiconductor, is a semiconductor technology used in microprocessors, static RAM, and camera video sensors. The CMOS sensor is a more complicated device than the CCD (charge-coupled device) sensors used in some cameras. Many IP cameras use the CMOS sensors because of lower power required.
DDoS A Distributed Denial-of-Service is an attack over the Internet that comes from many different sources (IP addresses). Since the message traffic is very high and comes from different IP addresses, it is very difficult to filter.
DHCP Dynamic Host Configuration Protocol is a network management protocol used on UDP/IP networks. It uses a DHCP server to assign IP addresses to all the devices on the network. Each computer can request an IP address. It makes the network administrators job much easier since they don’t have to go around assigning static IP addresses.
DNS The Domain Name System provides nice names for all the computers on the Internet. Instead of having to remember that The IP address is 156.119.12.56, we can type in “Kintronics.com” and the DNS server will find our web server location. Now I forgot where I live…
DOA Dead on Arrival is used to describe a product that doesn’t work when it is received. This is an out-of-box-failure. It can also mean that the person was dead when the medical assistance arrived. Ugh!
DVD Digital Video Disc or Digital Versatile Disc is an optical disc. The originally DVD-ROM disc was developed in the 1990’s and was used in the consumer entertainment industry to store movie video, and in the commercial sector to store computer data. The information was stamped on the DVD-ROM disc and was read-only. The DV-R disc allowed us to record the data, while DVD-RW discs allowed us to write, erase and read many times.
DVR Digital Video Recorder is a device that records the analog video from analog CCTV cameras. The NVR (Network Video Recorder) has replaced the DVR because it supports IP cameras.
EEPROM The Electrically Erasable Programmable Read-Only Memory is non-volatile storage used in computers. This is different than the EPROM which is Erasable Programmable Read-Only Memory. Both can be erased, and new data can be written to it, but all the memory stored in an EPROM is erased at one time by using an ultraviolet light source, while the EEPROM can electronically change one byte at a time.
eSATA This External Serial AT Attachment that is used to connect hard drives to a computer bus interface. Hard drives and optical drives use this interface. This is a form of SATA that provides better cable connections and different voltage levels that are designed for external drive connections.
FTP File Transfer Protocol is a network protocol standard that is used to transfer files between a computer server and a client.

FUD Fear, Uncertainty and Doubt is a disinformation strategy used in sales, marketing, and propaganda. It is used to spread false information that could create fear and uncertainty. I think we are all familiar with this disinformation tactic. We sometimes refer to it as “Fake News” which is specifically related to journalism. I was reading all the Facebook posts the other day and I got so confused I started to doubt the recipes articles.
GB and Gb There is a difference between GigaByte (GB) and GigaBit (Gb). The prefix Giga stands for a large number with 9 zeros (1,000,000,000 or 109). The Gigabit has 109 bits. The Gigabyte has 109 bytes. Since a byte has 8 bits, the gigabyte contains 8 Gigabits.
GUI The Graphical User Interface uses graphical pictures or icons to help users interact with their computer. The concept is to make it easier for people who don’t like text navigation. The Apple Macintosh computers were the first popular use of GUI. It made the computer more user-friendly.
HTML Hypertext Markup Language is what we use to bring you this web page. It’s a markup language for defining what the web page will look like. The HTML elements are the building blocks of the web page. The web browser interprets the HTML elements to provide the display. It allows us to define the text, add images, and provide nice formatting to make the page look nice.
Hz Hertz is a unit of frequency defined as one cycle per second. The power used in the United States has a frequency of 60Hz. WIFI radios use 2.5 GHz and 5 GHz frequencies. Sound can also be measured in Hz. Voice frequency is about 300 to 3000 Hz. The Hertz is named after Heinrich Hertz who proved the existence of electromagnetic waves and has led to among other things, people wearing tin-foil on their heads.
IP Internet Protocol is the communication process used on the Internet. IP helps information move from point to point on the Internet. This protocol is usually used with the Transmission Control Protocol (TCP) and together is usually referred to as TCP/IP. The task of IP is to deliver packets of data from one host to another. Among other things, it includes the address of the source and the destination. TCP provides a communication service between an application program and the Internet protocol (IP). TCP provides increased reliability of the connection.
I/O Inputs and outputs of a computer device. The term is used for general communication between the computer and an external device, but in IP cameras we have very simple “on” or “off” states. For example, the Input of an IP camera can be used to sense that a button has been pushed. The output connection can be used to sound an alarm or open a door. The camera provides low-level power output so if you want to open a door, you need a relay to provide the higher power required by the electric lock.
JBOD Just a Bunch of Disks (or drives) is what it sounds like. Instead of arranging disk drives in a RAID configuration, the drives are attached as individual disks that can be used independently.
JPEG A standard from the Joint Photographic Experts Group. It is a graphics compression scheme that is used for encoding digital images. It is also part of the M-JPEG (Motion-JPEG) format where each frame of a video is compressed separately.

MAC Address The Medium Access Control Address is a unique identifier assigned to a network interface controller (NIC) for network communication. Every network attached device, such as an IP camera or a network attached door reader, have unique MAC addresses. The MAC Address is used in the in the data link layer of a network. The MAC protocol is part of layer 2 of the OSI (Open System Interconnection Model) network model. Along with the Logical Link Control (LLC), it makes up the Data Link Layer.
MJPEG Motion JPEG is a compression scheme used in IP camera video compression and transmission.
MPEG The Moving Picture Experts Group is a working group of professionals that define a set of standards for audio and video compression and transmission.
MPEG4 MPEG-4 Is a video compression scheme that improved on the MJPEG compression by introducing the concept of transmitting only the parts of the video that are moving (objects). For example, if a person moves across a field only the person’s movements are sent from frame to frame rather than the field and person. New compression schemes such as H.264 and the latest H.265 compression schemes provide much better compression.
MTBF Mean Time Between Failure is the predicted time between failures of electrical equipment. This term is supposed to be used to define the elapsed time between failures of equipment that can be repaired. I have seen this used for IP cameras and other devices that are not repairable. For non-repairable devices, we should use MTTF or Mean Time to Failure. Once it fails, you throw it away.
NAS Network Attached Storage is a computer storage device that connects to the network and can be shared by multiple computers. NAS usually includes RAID, which is a Redundant Array of Independent Disks (or maybe … Inexpensive Disks). RAID provides increased reliability and can operate even if one of the disk drives fails.
NTSC National Television System Committee is the analog television color standard used in North America. The early video surveillance camera systems used NTSC. Engineers joked that NTSC stood for “Never the Same Color” because of the uncertainty of this analog technology.
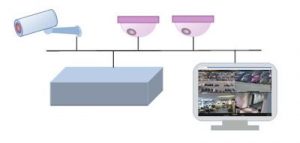
NVR The Network Video Recorder is a network-attached device that manages and records the video from IP cameras. The NVR is a specialized network attached computer system with hard drives for recording the video. There are NVR systems that include network connections for each IP camera, and there are others that utilize separate network switches to connect to the IP cameras and the general LAN network. This is different than the DVR (Digital Video Recorder) which recorded video from analog video cameras. The software used in an NVR is similar to Video Management Software (VMS) that runs in a general PC.
NVR The Network Video Recorder is a network-attached device that manages and records the video from IP cameras. The NVR is a specialized network attached computer system with hard drives for recording the video. There are NVR systems that include network connections for each IP camera, and there are others that utilize separate network switches to connect to the IP cameras and the general LAN network. This is different than the DVR (Digital Video Recorder) which recorded video from analog video cameras. The software used in an NVR is similar to Video Management Software (VMS) that runs in a general PC.
OnSSI On-Net Surveillance Systems is a software company that was founded in 2002. The company provides video management software (VMS). Their Ocularis 5 software is a multi-server multi-client solution that manages IP cameras and records video.
PoE Power over Ethernet is a method of including power along with the data over an Ethernet cable. There are various techniques for providing PoE using the same wires as the data or using different wires in the same cable.
RAM Random-Access Memory is semi-conductor data storage. RAM is used to hold the current program and data used by the computer. The data is usually held in Dynamic Random-Access Memory (DRAM) which is a volatile memory that is lost when the computer power is turned off.
RFID Radio Frequency Identification is the technology used for reading information on credentials (tags or cards) from an RFID reader. There are short range and long-range credentials. Take a look at our article about How Long-Range Access Control Systems Work.
SaaS Software as a Service is a software delivery system that is licensed on a subscription basis rather than an on-site license. Software subscriptions have become more popular because they provide almost instant delivery and updates. As an example, Pure Access door control software from Isonas is provided on a subscription basis. The yearly charge is based on the number of IP door readers supported.
SDK Software Development Kit is a set of programming development tools that make it easier to interface with another program. The SDK can work with application programming interfaces (APIs). An API provides the rules or command structure for interacting with another program.
UDP User Datagram Protocol is one of the Internet protocols. UDP uses a simple communication mechanism that doesn’t include any handshaking between devices. This provides very quick communication but can be unreliable. There is no guarantee of delivery that is provided by TCP/IP protocols.
VGA Video Graphics Array is a graphics standard for the video display controller. The original standard used a 15-pin D subminiature connector and provided 640 x 480 resolution. This standard was also used by early analog surveillance video cameras.
VMS Video Management Software is used to manage and record the video from IP cameras. It is one of the ways to record video from IP camera systems.
VoIP Voice over Internet Protocol is a methodology for delivering voice communications over IP networks. This digital technology is the next generation for analog telephone technology. SIP (Session Initiated Protocol) is a standardized VoIP protocol. VoIP can be used in phone systems, Intercoms, and IP paging systems.
WDR Wide Dynamic Range is the method used by digital cameras to increase the light range of IP cameras. For example, it is difficult to see a person standing in front of a bright window. By adjusting the camera, you can either see the person or the background. High Dynamic Range(HDR) is a similar technique used by cameras in our smartphones.
If you would like to learn more about any of the computer and network acronyms and abbreviations, just contact us at 1-800-431-1685 in the USA, or at 914-944-3425 everywhere else, or use our contact form.